SERVICES
AWS Cloud Architecture, DevOps Experience
Amazon Web Services (AWS) offers unmatched scalability, reliability and security for startups and big business alike. We host all our mission critical client systems on AWS.
E7 Systems has developed and operated a number of high performance, high availability systems utilizing the Amazon Web Services (AWS) infrastructure. E7 Systems has managed tens of millions of transactions annually worth over 10 billion dollars. Every year we have achieved PCI Level 1 certification running on AWS. Cloudwatch and E7 proprietary tools make it easy for us to provide 7x24x365 support for any AWS hosted system.

services
AWS High Availability Architecture
EC2 with Elastic Load Balancing
Route 53 DNS
RDS (Relational Database Service) Replication
Functional Redundancy – Separate servers for non critical functions
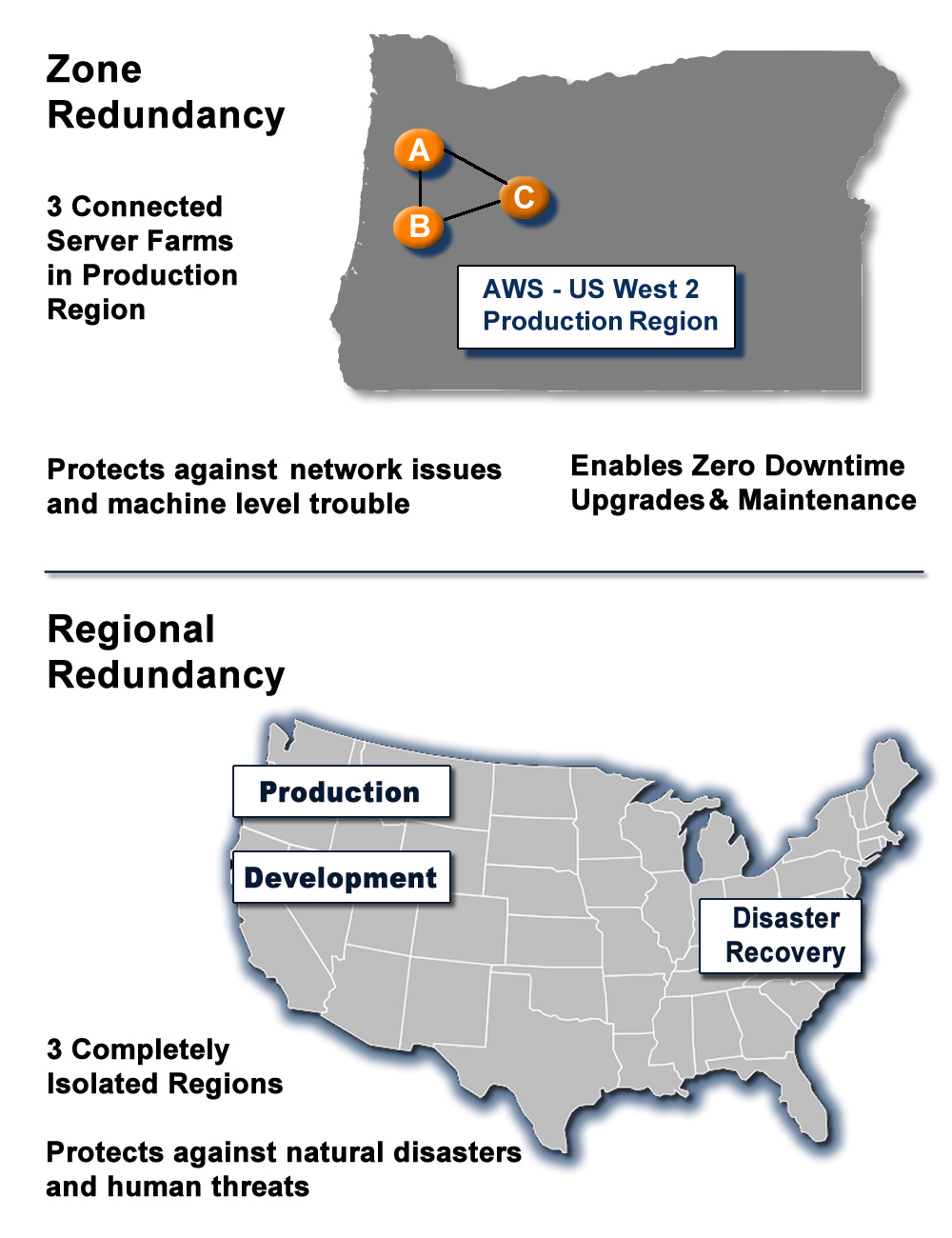
Zone Redundancy – Load Balancing
Disaster Recovery hot backup via replication across AWS regions
Disaster Recovery plans and procedures
Professional level Incident response tools and procedures
Operating System Level early detection and notification systems, using AWS Cloud Watch
System Application Level early detection and notification systems, using proprietary software.
Automated release procedures within TeamCity, Slack, GitHub & Jira
Continuous Integration with Jenkins
services
AWS Cloud Security and PCI

Multifactor Authentication by DUO
Bastion server for admin ingress
AWS Security Groups
Development Machine Instances hosted in AWS EC2 machines to control PCI scope
Integrated 3rd party security tools for asset discovery, vulnerability management, intrusion detection, behavioral monitoring, SIEM, log management, and continuous threat intelligence
Integrated
Complete and custom integration of AlienVault Unified Security Management (USM) for AWS
Professional level Attack response and prevention
Tools for prevention of DDOS, Brute force, and Tier-1, 2 & 3 level attacks
AWS Network Access Control Lists (ACL)
Client IP collection and whitelisting
Penetration Test Compliance
PAN Data Scanning (exhaustive search for card numbers) and Compliance
External and Internal Firewall configuration and management.
Encryption and certificate configuration and management across load balancers.
Secure Integration with Third-Party Service providers like First Data
Network Segmentation to isolate instances and services in and out of PCI scope
Integration and security of connected hardware components like ATMs, PoS terminals, card readers, ATM machines and scanners.

PCI_DSS_Attestation_of_Compliance_(AOC)
PCI Training procedures and certifications
Vulnerability Management programs
Access Control Systems
Monitoring and Test procedures
Risk Mitigation
Network and Infrastructure monitoring and audits
Log management and security
Data retention and disposal
PAN masking and encryption
Secure development environments and management
Strong cryptography and security protocols
Vulnerability assessment and management
Documentation Best Practice and Procedures
Strong policy development practices for internal and external software applications (including web-based administrative access to applications) securely including code review, secure repository and deployment standards
Background checks on all team members
services
7 x 24 x 365 Monitoring & Control
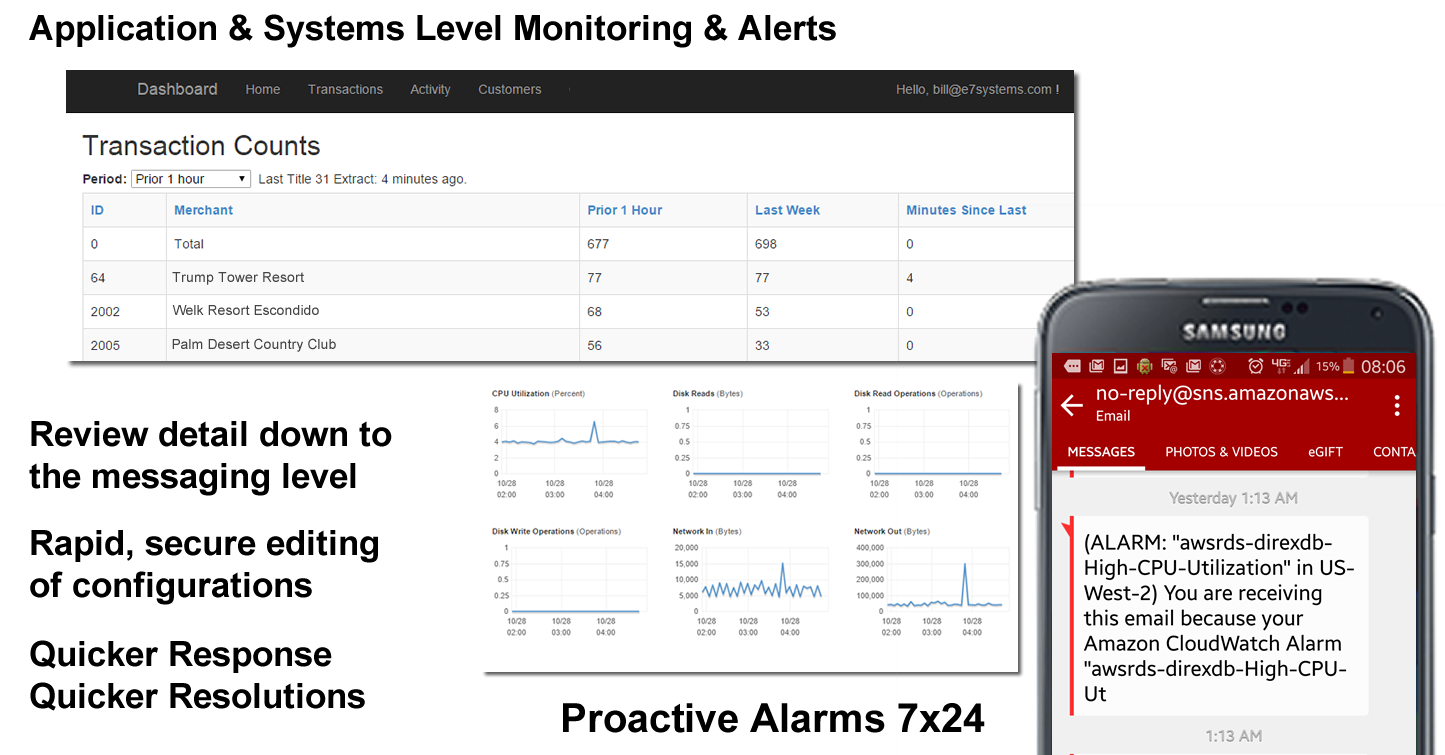
When your system needs 100% uptime, redundancy and cloudwatch are not enough. You need application level tools that will watch the application behavior and report any exceptions immediately to qualified engineers who can quickly assess and act on any situation.
